- Download John the Ripper - John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS.
- John the Ripper determines the hash type of the password file and then attempts to find a match for those hashes. This tool also highlights the importance of choosing a strong randomized password. Cracking passwords found in a word list is 10-fold faster than running an incremental brute-force attack.
John the Ripper is a fast password cracker. Its primary purpose is todetect weak Unix passwords. Besides several crypt(3) password hash types,supported out of the box include fast built-in implementations of SHA-cryptand SunMD5, Windows NTLM (MD4-based) password hashes, various macOS andMac OS X user password hashes, fast hashes such as raw MD5, SHA-1, SHA-256,and SHA-512, various SQL and LDAP server password hashes, as well as manynon-hashes such as SSH private keys, S/Key skeykeys files, Kerberos TGTs,encrypted filesystems such as macOS .dmg files and 'sparse bundles',encrypted archives such as ZIP, RAR, and 7z, encrypted document files suchas PDF and Microsoft Office's - and these are just some examples.
Read more at:
This version integrates lots of contributed patches, including GPU support,dynamic expressions, has fallback for CPU SIMD extensions and for OMP,moreover, has on device mask acceleration and prince mode available.
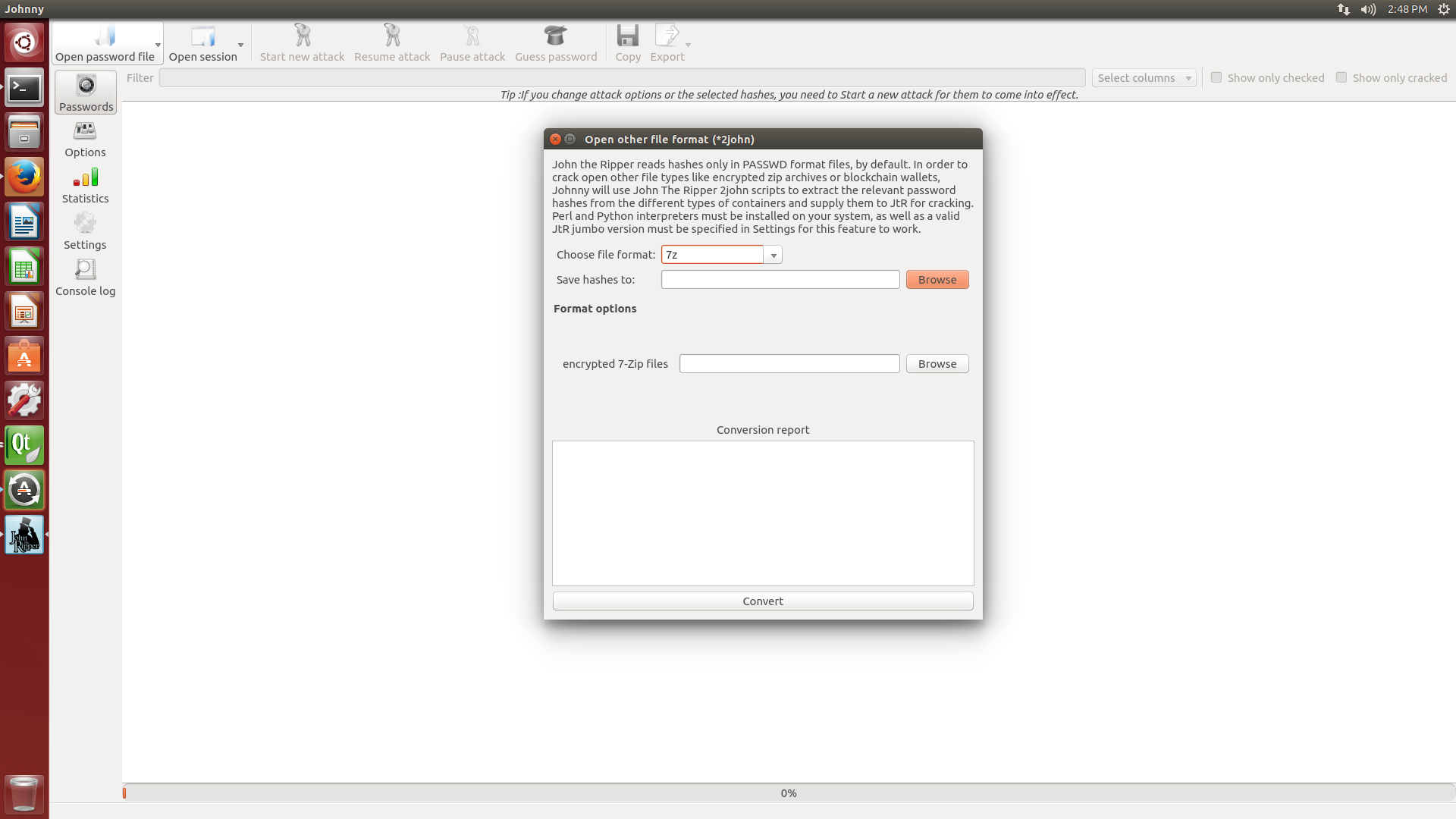
Choose which x2john program to run online and extract a hash that can be used with JohnTheRipper or Hashcat
Popular
John The Ripper, AKA John/JTR is the extreme opposite of intuitive, and unless you are an UberGeek, you've probably missed out few subtleties. Secondly, John The Ripper is a bit like a Muscle Car delivered from the factory with the 'Eco' settings enabled by default. If you want the 'Muscle', you'll have to open the hood. Mar 15, 2020 John the Ripper is a fast password cracker which is intended to be both elements rich and quick. It combines a few breaking modes in one program and is completely configurable for your specific needs for Offline Password Cracking. Getting Started Cracking Password Hashes With John the Ripper.
bitcoin2johnExtract hashes from Bitcoin and Litecoin wallet.dat files
pdf2johnExtract hashes from encrypted PDF .pdf files
rar2johnExtract hashes from encrypted .zip or .rar or .7z files
zip2johnExtract hashes from encrypted .zip or .rar or .7z files
7z2johnExtract hashes from encrypted .zip or .rar or .7z files
office2johnExtract hashes from encrypted Microsoft Office files (.doc, .docx, .xls, .xlsx, .ppt, .pot)
itunes_backup2johnExtract hashes from encrypted iTunes backups Manifest.plist
ethereum2johnExtract hashes from encrypted Ethereum wallets (Geth/Mist/MyEtherWallet)
monero2johnExtract hashes from encrypted Monero wallet .keys files January 2016 or later
gpg2johnExtract hashes from encrypted GnuPGP .asc files
Other
bitlocker2johnExtract hashes from encrypted Bitlocker volumes
bitwarden2johnExtract hashes from Bitwarden storage.js / com.x8bit.bitwarden_preferences.xml / Google Chrome's 'nngceckbap...'
blockchain2johnExtract hashes from Blockchain.info v1, v2, v3 wallets
dmg2john
Extract hashes from encrypted .dmg files
filezilla2johnExtract hashes from Filezilla Server .xml configuration file
keepass2johnExtract hashes from encrypted Keepass .kdb .kdbx files
keychain2johnExtract hashes from Mac OS Keychain file ~/Library/Keychains
keyring2johnExtract hashes from Keyring file ~/.local/share/keyrings
keystore2johnExtract hashes from encrypted .keystore / .jks files
money2johnExtract hashes from Microsoft MS Money 2002-2007 / Money Plus file
mozilla2johnExtract hashes from Mozilla Firefox password database key3.db file
padlock2johnExtract hashes from encrypted Padlock files
pem2johnExtract hashes from encrypted PEM/OpenSSL .pem files
putty2john
Extract hashes from encrypted PuTTy .ppk files
pwsafe2johnExtract hashes from encrypted PasswordSafe .psafe3 files
John The Ripper Mac Dmg
signal2johnExtract hashes from encrypted Signal messages SecureSMS-Preferences.xml
ssh2johnJohn The Ripper Mac Dmg Torrent
Extract hashes from SSH Private keys
staroffice2johnJohn The Ripper Download
Extract hashes from encrypted StarOffice files (.sxc, .sdw, .sxd, .sxw, .sxi)